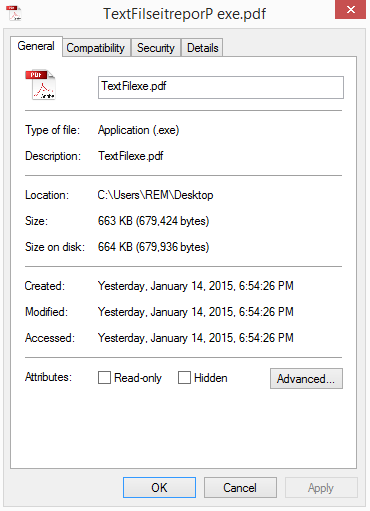
After running a few malware samples in a virtual machine, it becomes obvious that malware developers thrive on social engineering. Why bother waiting for a zero day when you can just attack human error? Here are a few social engineering attempts I’ve seen so far:
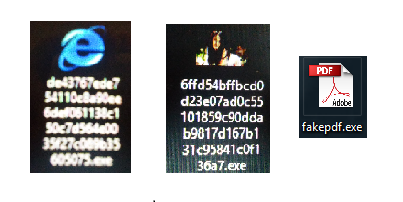
I would say the most common “spoofed” file type is probably a pdf. So it’s a good idea to think twice before visiting a dodgy site to save money on textbooks.
More advanced users know that to run an exe in Windows its necessary to use the file extension “.exe”. If a malware developer wanted to distribute a file that was still executable but looked like a pdf it would still have to be called something like “myevilfile.pdf.exe”. The alternative of course is to use a pdf viewer exploit but not every system will be running a vulnerable pdf viewer. File extensions are hidden by default on windows so leaving the file name as “.exe” can still be effective.
But what if a user DOES have file extensions enabled? An “.exe” extension for a pdf may immediately throw some red flags. A malware developer could use some clever Unicode characters to flip the file extension name. This trick was originally described by Lyle Frank from the Avast blog: https://blog.avast.com/2011/09/07/unpacking-the-unitrix-malware/
The magic happens with the Unicode character U+202E called “Right-To-Left-Override” what this character does is flip all characters to the right of it over a central axis. For example a file called “eci.exe” that has the Unicode character U+202E inserted in front of it will appear as “exe.ice” the file name is flipped over the dot.
The trick is pretty simple for a malware developer to deploy. Just open up All Programs-Accessories-System tools-Character Map then copy the character and paste it into the file name after right clicking.
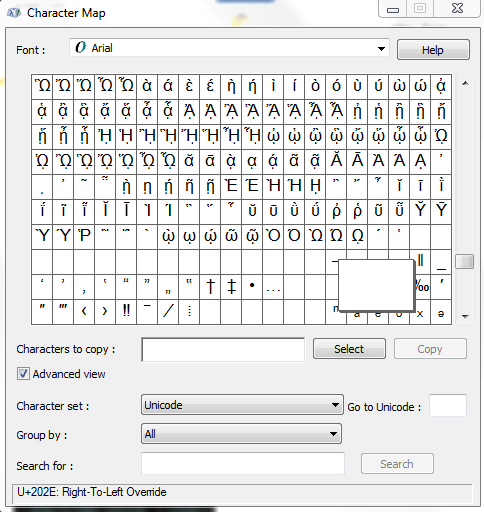
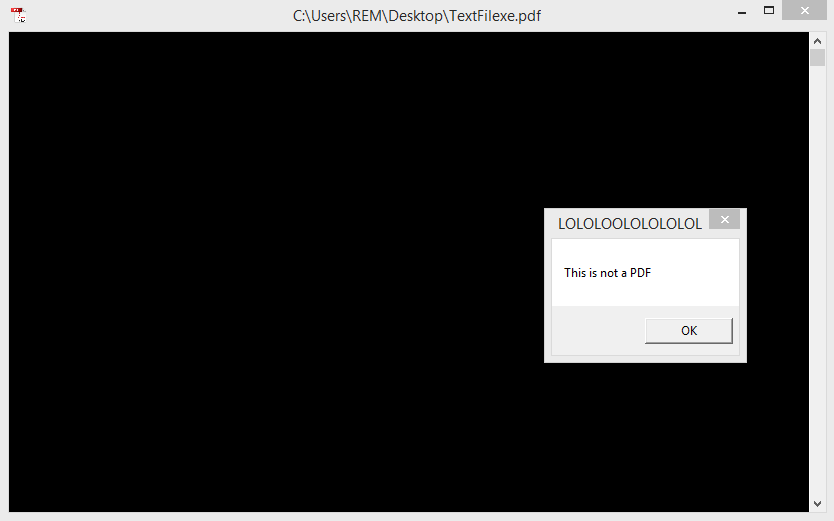
In the picture bellow the file was originally named “TextFilfdp.exe” After inserting the Unicode character after the letter “L” the file name appears as “TextFilexe.pdf”
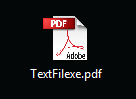
When double clicked, the file produced the ouput below. For a malware developer though, it would make sense to have the exe launch a real pdf viewer as a sub process. Then, while it’s open, have the malware inject itself into the real pdf viewer using dll injection quietly.
On windows, I recommend right clicking on the file and viewing its properties to verify its file type before double clicking.